dns.cmrg.net lets you keep what you look up in the DNS a
secret from anyone snooping on your network traffic.
This is a privacy-preserving open DNS resolver, offering only DNS-over-TLS (a.k.a. DoT, RFC 7858).

To use this on an Android device, go to:
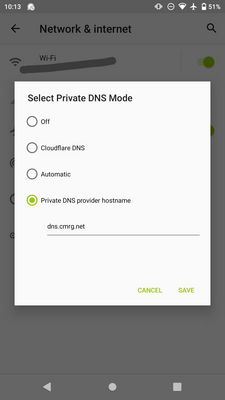
Settings → Network & internet → Advanced → Private DNS
Select “Private DNS provider hostname”
In the “Enter hostname of DNS provider” field, put
dns.cmrg.net
To uninstall, just go back to the same setting and set it back to “Automatic”.
Load this mobileconfig file.
For iOS, the device will prompt you to confirm that you want this setting. Once you agree, you need to open the Settings app.
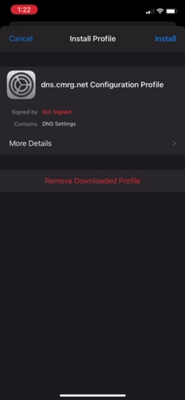
Near the top of Settings, you’ll see “Profile Downloaded”. Tap it, then tap the “Install” button in the top right of the “Install Profile” page.
You’ll be prompted for your password. Once you’ve entered it, you have to tap “Install” a few more times to confirm.
You may see warnings that this profile “is not signed” because we haven’t paid for the credential iOS requires for this purpose.
To uninstall, go back to the Settings app, choose “General”, and scroll down to “Profile” where it says “dns.cmrg.net Configuration Profile”. Tap it, you’ll see a screen of all profiles you have loaded (maybe just this one!). Tap “dns.cmrg.net Configuration Profile” again, and you’ll see a button to “Remove Profile”.
You’ll need to enter your password for removal as well.
| hostname | dns.cmrg.net |
| IPv4 address | 199.58.83.33 |
| IPv6 address | 2001:470:1c:76d::53 |
| TCP port | 853 or 443 or 53053 |
| OOB Pins | 3IOHSS48KOc/zlkKGtI46a9TY9PPKDVGhE3W2ZS4JZo= 5zFN3smRPuHIlM/8L+hANt99LW26T97RFHqHv90awjo= |
To use this on a modern Debian system, you can set up a local forwarding stub resolver with:
apt install knot-resolver ca-certificates
cat >> /etc/knot-resolver/kresd.conf <<EOF
policy.add(policy.all(policy.TLS_FORWARD({
{'199.58.83.33', hostname='dns.cmrg.net',
ca_file='/etc/ssl/certs/ca-certificates.crt'},
{'2001:470:1c:76d::53', hostname='dns.cmrg.net',
ca_file='/etc/ssl/certs/ca-certificates.crt'},
})))
EOFAnd then ensure that /etc/resolv.conf points to the
local resolver:
# /etc/resolv.conf
nameserver 127.0.0.1This service does not log queries beyond the time window necessary for debugging service failures by system administrators. We do not share log information with anyone for any other purpose.
Ths service pads DNS-over-TLS responses on port 853 according to common practice, as derived from empirical research. Ports 443 and 53053 do not offer padding, so response sizes are visible on the wire. It is strongly recommended that your DNS client also pads its queries for maximum protection against size-based traffic analysis.
Added IPv4 address 199.58.83.33, replacing older 199.58.81.193. The old address will still function for several months at least.
Given the technical capacity, the following upgrades are intended (not necessarily in this order):